SSH Key Authentication
The Secure Shell (SSH) is a protocol for secure remote login and other secure network services over an insecure network.
How SSH Key Authentication Type Works
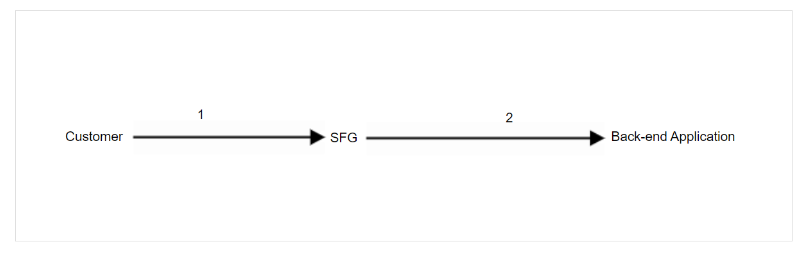
FIGURE 1: Customer Pushes File
In Step 1, the customer pushes files to SFTP Server. The following process steps must first occur for this transfer to be successful:
- The MFT team provides the user account credentials for SFTP Server to the customer.
- The customer must provide their SSH Key to the MFT team.
- The MFT team uploads that SSH Key into SFTP Server, and attaches that key to the SFTP Server user account they created for the customer in Step 1.
The above steps enable SSH Key authentication for the customer when they send files to SFTP Server.
Installing SSH Keys
Teams need to execute the commands to install SSH keys on any system and for any user that does not already have SSH keys setup. If a particular user on a system already has SSH keys set up, then all these steps do not have to be done. For example, if the keys are already set up, then you either need to add a key to your authorized_keys file, or share your .pub key with the other party. To determine if keys are already set up, check the .ssh directory.
To install the SSH Keys, complete the following steps:
- Create a 4096-length SSH Key-pair (this is not done by default):
- Enter ssh-keygen –b 4096 in the command line.
- Take all defaults, and hit enter until you are back at the command line.
- This creates a .ssh directory in the user's home directory, and two files in the .ssh directory, as shown below:
[{user}@{server}][/export/home/{user}/.ssh] > ls -ltr total 20
-rw------- 1 {user}{user} 402 Aug 31 20:26 id_rsa.pub
-rw------- 1 {user}{user}1675 Aug 31 20:26 id_rsa
- To allow for SSH Key Authentication (when a user logs in to your system), create an authorized_keys file in the .ssh directory :
- Paste the key(s) in the file without any spaces. Each key should go on a separate line, and should be one continuous line with no spaces, carriage returns, or breaks.
- The permissions on the authorized_keys file should be 600. Also, the permissions on the .ssh dir should be 700.
- The file and directory should appear as shown in the following example:
[{user}@{server}][/export/home/{user}/.ssh] > ls -ltr authorized_keys
-rw------- 1 {user}{user}804 Nov 1 21:48
authorized_keys
[{user}@{server}][/export/home/{user}/.ssh] > ls -ld .
drwx------. 2 {user}{user}4096 Nov 1 21:48 .
[{user}@{server}][/export/home/{user}/.ssh] >
- If you are attempting to use SSH Key Authentication to log in to another system, use the cat command on the *.pub file in the .ssh directory, and share the output with the person who owns that system, as shown below:
[{user}@{server}][/export/home/{user}/.ssh] > cat id_rsa.pub
ssh-rsa AAAAB3NzaC1yc2EAAAABIwAAAQEA4pMPSts1ahFEJ0/OxefQykhqFxbqWGYo7aQRUxabcdefg123456lpTKlllsglknsvdlknlkxbnloipnvx2146513v1tz8HXKjcDJORS5IDl2Pq9eAdJfhh1aat5kY9GtGE438rhOmBKjrVgF51i0JDy7hV9JPMw4QoIl4ePxMwhuu4SzCZcFgTmUjehlC0P3jFBsbt4LGccVpw7EccHTL47GUKho4mVXKJv2Cxk3Z7XLXbHGofY7MqobXfgWvRXkwk60xMoa0Cnqg4JDUBWw32pcugG8fOXUR+8n3r+p1CTaxQ3QPwYH6KzciPUUMC9AqStTAlQ== {user}@{server}
Download Public Key (New Version, 4096 bit)
4096-UAT-ED25519-AUTH-KEY-04202026-SHA256Z1pnDRkfX0XdMPu45r+KJjF04psG43dZFpI7nPmnQUg.pub - Expires Monday, 4/20/2026, 11:59 PM ET
4096-PRD-ED25519-AUTH-KEY-04202026-SHA256+eGBRAYQq5hIu4Wzbw0TG7NhOcXdLe2YB6FzjO0Oo - Expires Monday, 4/20/2026, 11:59 PM ET